Vetting a Provider
Lately, law offices all over the country have been turning to video conferencing to meet with clients, talk to teammates in their offices, and even attend remote hearings. But with the speedy move to these tools, I’d venture to guess that some of us are outside of our comfort zones, now. That’s okay. These are new paths we’re forging in how we communicate with our clients and others in the legal field. It can, understandably, take some time to acclimate to new methods.
As of this writing, I would imagine that most of us are using Zoom for these new meetings. That would make sense. Its easy to learn, quick to set-up, and convenient for all users. It even has a free tier if you’re able to keep your group meetings under 40 minutes. But please stop. Seriously. Don’t use it to communicate with your clients, or with anyone in your office about your clients. Don’t exchange sensitive information on the platform. Don’t share Personal Health Information on the platform. And don’t exchange client files over the connection. Just don’t.
Even without the Zoom Bombing issues out there, there isn’t enough privacy in the platform to be sure you’re maintaining client confidentiality. And since it doesn’t have end-to-end (E2E) encryption, your communications may not be privileged. Although Zoom literally changed their privacy policy four days prior to this writing, it’s not enough.
Look for something else.
And while you’re looking for that something else, read the privacy policy and properly vet the service. I get it, you’re not a computer surgeon. This isn’t super-fun for you. That’s okay, we’ll go through some steps for initially vetting your provider.
For the most part, you’ll want to look for two specific protections. First, what data does the platform share with third-parties (i.e. Google Ads)? And, second, what sort of security do they use for your data at rest (stored data) and your data in transit (moving over the internet)? Once you do this, if you determine that your client information is, or could be, accessible to a third party, use another provider. There are plenty out there.
So, what’s wrong with Zoom?
As a platform for hosting quick chats or virtual happy hours? Not much. It’s a good service that’s easier to use than many others. However, its privacy policy leaves a lot to be desired for attorney-client communications. And its lack of E2E encryption feels intentional.
No, but seriously, what’s wrong with Zoom?
Zoom shares information that it collects on you and your clients (the other users of the platform) with organizations like Google and Facebook in order to help those companies serve more personalized ads to you all over the internet. This is not a massive problem in the real world. But for attorneys, it means that you’ve now shared (or required your client to share) personal information about your client with a third party – possibly in violation of your ethical obligations.
This sharing becomes problematic when the data shared has personally identifiable information of our clients in it. And Zoom’s does. Zoom specifically says they may collect the name, address, and email address from you and your client when you use the platform (you likely give it to them when you sign up). They then go on to say that they send this information to third-parties like Google and Google Ads (but they call this “Marketing Communications”). Now, according the them, you can opt-out of this, or opt-in, or something like that – it’s hard to tell from the Policy (See Below). Zoom’s not super-great about being straightforward in their language.
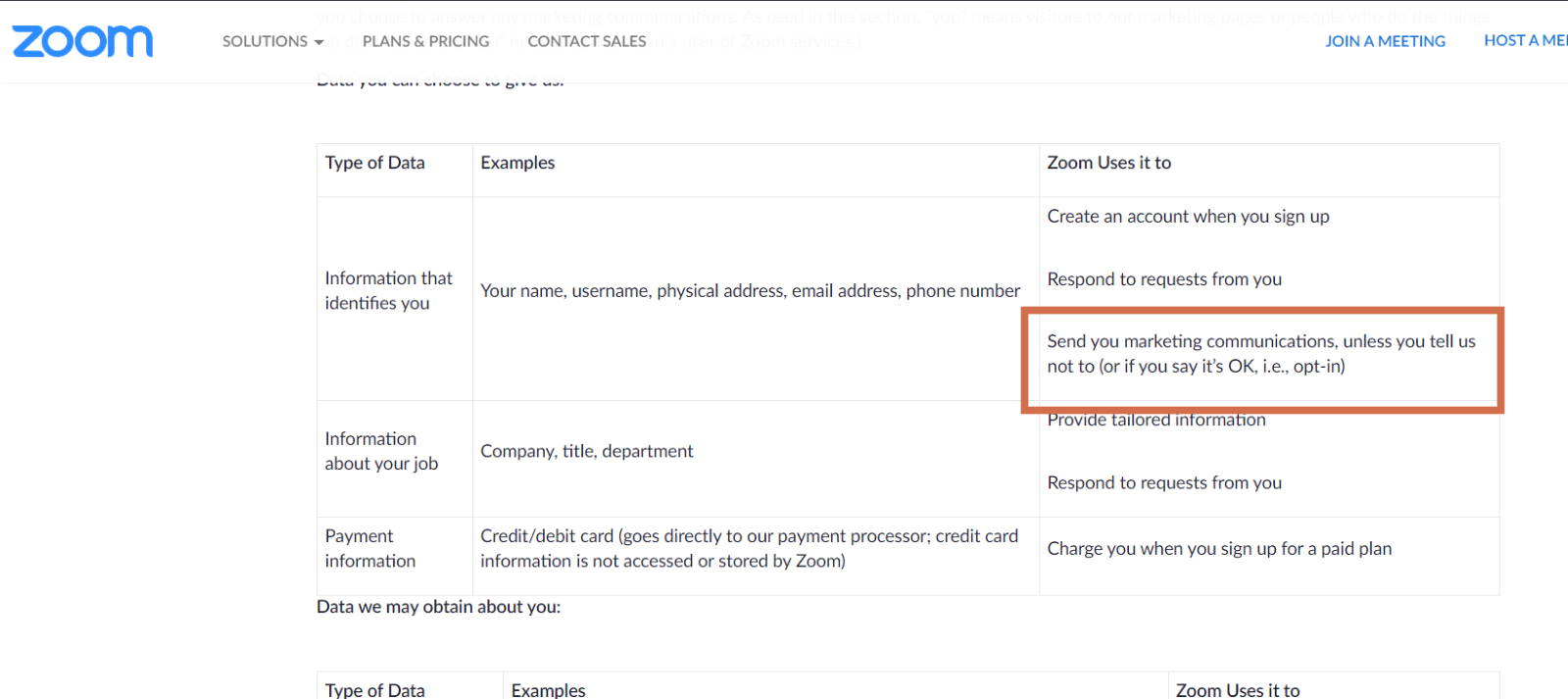
More importantly, however, as of this writing, communications over Zoom’s platform are not E2E encrypted. This means that while your communications are travelling from computer to computer, or computer to server, there is little to no protection from snooping third parties. Now, most people may not really care about that, but for attorneys, this means that you could have waived your attorney-client privilege. You’ve got a potential third-party listening into your conversation. So that’s fun.
How do we find a provider?
I know you don’t want to hear this but read the Privacy and Security Policies of your potential provider. In doing so, first, we need to know 1) what information do they collect about you and your client, and 2) who are they sharing that information with (if anyone)? Then we need to determine what sort of security they’re using to protect your information while it’s at rest and while it’s in transit.
What information do they collect?
As you probably know, some information gathering is necessary to run the site. Things like your IP address, browser type, and current operating system are all normal information for the platform to collect on its users. These are also likely not personally identifiable. If your provider were to share this information with a third-party, you probably wouldn’t be violating any ethical obligations.
It’s when providers collect and store more information than is necessary to run the site that we need to be concerned with. Specifically, pay attention to what the provider defines as personal information or personal data. With Video Conferencing providers, it’s likely they collect information about the user like their name, email address, phone number, and other personally identifiable data. Again, this is not inherently a problem. Keeping track of this information helps you use the platform in the way that you expect. In fact, you likely gave that information to them willingly when you sign up. It’s not nefarious – its part of the system. We want to know the names of the people we’re talking to, and may need to know their email address in order to send them an invite.
In addition to personal data, Video Conferencing platforms likely collect and store information that you create through the platform or share over their connection (User Created Content). There would be no way to go back and check the notes you took in a meeting if they didn’t. Again, not inherently nefarious. If they collected this information and then stored it on secure servers somewhere with no intention of sharing it with a third-party, that would be fine. The problem comes when another party has access to it. And this can happen in two ways: 1) your provider intentionally shares it, and 2) your provider unintentionally shares it.
Who do they intentionally share with?
Once we have an idea of what information our Provider is collecting on us and our clients, we can then make a determination as to whether this information is being kept appropriately private. We need to determine who they are sharing this information with, and whether or not we can opt-out of that process (and how difficult is the opt-out procedure).
Third-party sharing of user information from a website is not uncommon. Many platforms will share some of the data they collect with analytics providers like Google or Facebook for the user’s benefit. This actually helps them run the website. It helps determine how users enter and move through the site, as well as what sort of platforms they’re using to view it. This type of information can be very handy when trying to enhance the user’s experience or determining if there’s a problem with the structure of the site. However, it becomes an issue for attorneys when the information that’s shared is personally identifiable. While collecting names and addresses of your clients is not problematic, shipping that information to Facebook or Google so they can better their ad service is.
In some cases, like with the use of free Gmail accounts, a platform will give third parties access to the user created data that it collects (not just personal data like above). This is done in order to enhance the effectiveness of the advertisements on the platform – I can’t think of any reason a provider would need to do this for the Users’ benefit. Mining the contents of your communications can yield vast amounts of information about user habits and preferences for advertisers.
Now, in real life, this is just a way for the User to pay for the platform – it’s your monthly fee, if you will. Many times, we willingly exchange our information (even the contents of our conversations) for free access to a platform. For attorneys, however, this amounts to exchanging your client information for the access. And even with their permission to do so (which may help with the ethical violations), you’ll likely run into attorney-client privilege issues if you do so.
Who do they unintentionally share it with?
In addition to whether or not your provider plans to share information they collect with a third-party, you’ll also want to be aware of how they protect your data from unauthorized third-parties. What do they do with your data while it sits on their servers, and how do they defend your data while it’s traveling from place-to-place?
Data at rest
A complete discussion of data-security on your provider’s platform is an article (or entire website) for another time, and I don’t think anyone would expect a typical user of a platform to be able to decipher which practices are better than others. For our purposes (since we likely only have an obligation to act reasonably), you’ll want to make sure that the provider states that they’re using generally accepted security practices in the field, or something to that effect. Bonus points if they store your data in a place that has based its reputation on security (Amazon Web Servers, Microsoft Cloud, etc…). If it’s unclear as to whether their practices are good enough, then either ask the provider to clarify, or choose a different provider. If you have particularly sensitive information that you’ll be exchanging over or storing on the platform, you may want to get a data-security consultant to vet the system for you. Many states now require us to be up-to-date on technology issues, so I doubt we will be able to plead ignorance on this one.
Data in transit
For the most part, the security of data-in-transit has one main requirement. E2E encryption. If your provider uses it, great (I mean, it’s pretty standard, they shouldn’t really get a cookie for it, but great). If they don’t, use someone else. Without end-to-end encryption, your provider has failed to protect the content of your conversations from a third-party. It’s like talking on a phone that you know has the potential to be tapped. None of us would do that, unless there were extremely strong countervailing factors. If you have any question as to whether they use E2E encryption (for some reason, they don’t state it in their policy), ask your provider to clarify or use another service.
Conclusion
Ideally, the provider you choose wouldn’t share any data they collect on you or your client with a third-party. However, that’s an unlikely scenario with a cloud Video Conferencing provider. Sharing aggregate, non-personally identifiable information helps the system work better for the user. Fortunately, you and your client can change your browser settings to protect against this. What we want to avoid, however, is a provider who shares personally identifiable information about your client, or allows a third-party to mine user-created content. This is not something we can protect ourselves from beyond a potential to “opt-out” with the provider.
Additionally, and I didn’t think I was going to have to say this about Video Conferencing systems, but make sure your provider uses generally accepted practices to protect your data on their servers and they use end-to-end encryption to protect the data while its moving. It’s ridiculous that any provider would fail to do this, but it happens. Look at Zoom.

